MEDINA aims to develop an innovative mechanism for supporting continuous monitoring of cyber security certification compliance for cloud services. Following a reputable standard is often considered as an approach for assuring high level of cyber security. At the same time, some requirements from a certification scheme defined for a wide range of cloud services may be not very relevant for a concrete Cloud Service Provider (CSP). Naturally, a strict approach following the Draconian laws, demanding fulfilment of every single requirement of a certification scheme, can be followed; but this good-for-all approach to security neglecting specific needs of CSPs is hardly practical and will not be easily accepted by potential users. In other words, there is a need for a decision-making mechanism that will be able to evaluate the degree of non-conformity with the selected certification schema considering the concrete needs of the CSP. In MEDINA, risk assessment is applied as a solution for this problem.
Cyber security risk assessment is a well-known instrument for evaluation of cyber protection of a system. It glues the technical and management views helping to analyse specific security features and abstract the results up to the system-wide level allowing for strategic decision-making. The key advantage of risk assessment is its focus on the concrete needs of the system. On the other hand, in scope of MEDINA we ground the assessment in a concrete cyber security certification scheme, considering it as the most complete selection of possible security features, omitting which opens a way (a vulnerability) for a threat to occur.
MEDINA aims to develop an automatic tool for management of continuous compliance verification process. This goal also imposes the demand for automatic processing on its integral parts, including the risk assessment engine. In other words, risk assessment process must be quick, simple, and human-independent. Most of risk assessment approaches are very long, require good knowledge of cyber security and heavily rely on the analyst.
For implementing the risk assessment functionality, we employ a Self-Assessment Tool for Risk Analysis (in short, SATRA), developed by the National Research Council (CNR). SATRA is implemented as a service which helps to conduct cyber risk assessment with minimal knowledge of cyber security; the user is assumed to know only the security practices applied in the system and the main assets which can be compromised by a successful cyber attack.
Similar to other risk-based approaches, the applied method is based on identifying, evaluation and analysis of the three basic sets of risk components: vulnerabilities, assets, and threats. The knowledge about cyber security practices is collected with a questionnaire and the lack of implementing some of the queried security features is treated as an existing vulnerability.
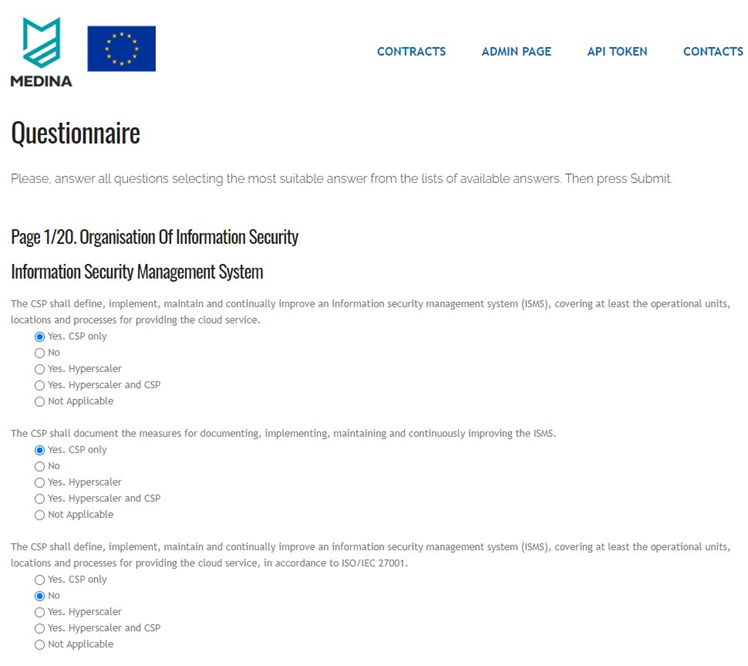
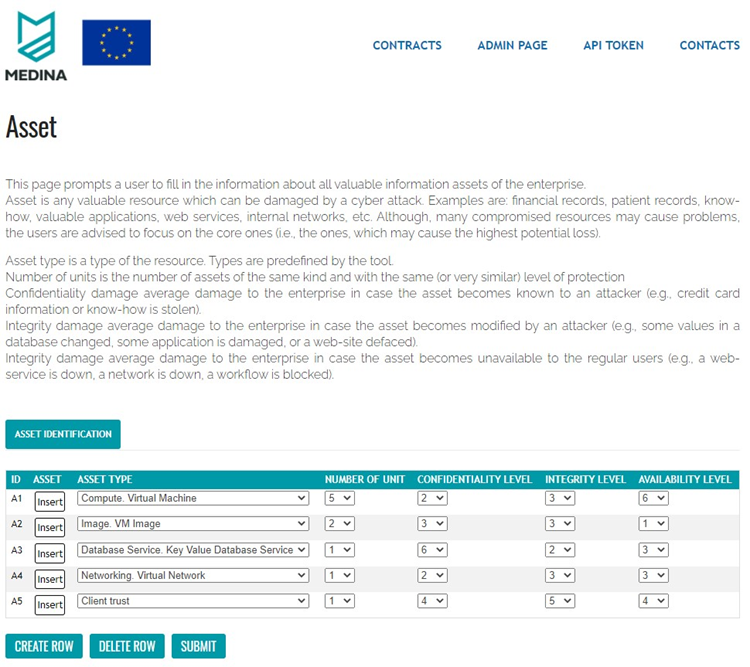
Assets are provided by filling in a special table, which also collects details about these assets, like the type of assets and expected impact for confidentiality, integrity and availability in case of a successful attack compromising this asset. The tool contains an exhaustive predefined list of possible threats (which may result in an attack) for a selected application domain.
Once the input information is provided the engine applies the internal logic for estimation (e.g., how well certain security controls are implemented), analysis (estimating the probability of a threat to occur assuming estimated security control implementation coverage or how much a threat occurrence (an attack) may cost) and final computation of risks: the overall risk per system and ranked risks per threats). Although our approach is based on pre-defined values (e.g., the list of queried security features and threats are limited and internal relations are established according to the embedded knowledge) it provides a quick assessment mechanism, which can be used for automatic decision-making without human involvement.
In scope of MEDINA, SATRA was set up for cyber security risk assessment in the cloud domain. First, the questionnaire used for collecting the knowledge about the applied cyber security practices is formed by the requirements of the certification scheme, selected by the CSP. Second, asset types are defined using typical resources used by cloud services (e.g., virtual machines, databases, CI/CD workflows, etc.). The exhaustive list of resources is defined by an ontology developed by Fraunhofer, one of MEDINA’s partners, and supported by automatic resource discovery engine as a part of Fraunhofer’s Clouditor tool. Finally, the list of threats has been tailored for including typical threats for cloud computing (such as account hijacking or poor control panel).
SATRA is to be used in two scenarios. First, it will be used as a standalone tool, which helps a CSP to prepare their system for certification. A CSP could manually insert the required information in order to analyse how far it is, in terms of risk, from full compliance. This analysis will let the CSP know if the non-conformity is significant (major) or not (minor). In case of major non-conformity CSP must improve its system. In case of minor non-conformity, the CSP may use the results of the analysis to advocate in front of an auditor that its system covers the requirements well, and the existing deviations are insignificant. Moreover, CSP may use the results of the analysis (a generated report) as a proof of performing risk assessment, which is a common requirement in cyber security certification guidelines.
But, MEDINA goes beyond this static analysis and aims to provide support for dynamic assessment. During the continuous monitoring phase, risk assessment will help to analyse the current state (measured by various assessment tools of MEDINA) and estimate the degree of non-conformity on the fly. It is important to note that in the ideal case, when all requirements from a selected certification scheme are measured, SATRA tool does not need a human to provide the knowledge about the implemented security practices. Furthermore, the automatic resource discovery tool (Clouditor) will be able to identify the available assets. This will significantly reduce the burden for setting the SATRA tool up, will make it possible to perform risk assessment with always up-to-date information, and will completely eliminate the need for human intervention during the continuous monitoring phase.

0 Comments