As a Research and Innovation Action, the MEDINA project aims at developing new approaches to support the automated certification of cloud services. A big challenge in the security assessment of cloud services is to connect and aggregate the isolated assessment results of different tools and different layers of a cloud system. One such layer is the software which can exhibit security flaws, like misconfigured security libraries, while another is the infrastructure layer which can be misconfigured in various ways as well, for example regarding the accessibility of storages or encryption of data transmissions.
Moreover, security measures must be coordinated between software security and infrastructure security: Encryption and authentication mechanisms, for instance, can be implemented in software and in infrastructure configurations – which can be a source for a lack of security measures or conflicts of implemented measures.
Bridging the Gap: The Cloud Property Graph
With the Cloud Property Graph (CloudPG) we propose an approach that directly combines software- and infrastructure-layer assessments in cloud systems. It uses an existing code property graph library (the cpg) which analyzes source code (i.e., the software-layer) and enriches the graph with deployment information of the cloud system (i.e., the infrastructure-layer) where the code is deployed. An example excerpt of such a property graph is shown in Figure 1.
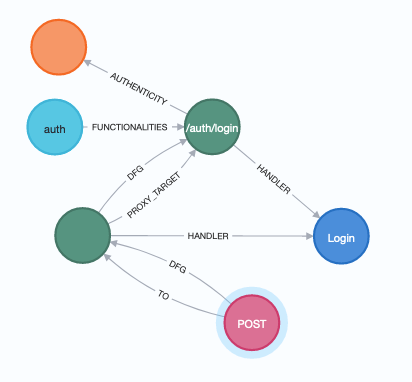
Figure 1: An excerpt from the analysis result of the Cloud Property Graph on an example application: It shows that an HTTP POST request is sent to the “/auth/login” endpoint, which in turn is part of the “auth” microservice, and forwards the request to the ”Login” function. It also shows that the endpoint does have an Authenticity configuration set; it does not, however, have an encryption configuration. To detect such security flaws, a simple query written in an SQL-like query language can be used.
Theoretical Background: An Ontology of Cloud Resources
The nodes that the CloudPG creates in the graph are based on a pre-defined ontology of cloud resources and their security features. For example, it defines computing, storage, and networking resources, and defines their security features like encryption and authentication mechanisms. One such computing resource defined in the ontology is a Container, while a networking resource may be a LoadBalancer.
The CloudPG then queries the cloud system to get information on deployment configurations and creates dedicated nodes and edges in the graph – based on the ontological concepts. For example, it may query the Kubernetes cluster that the application is deployed in to add dedicated nodes for the containers and load balancers in the cluster, and it enriches these with information about their geolocation.
The graph thus represents an abstraction of the cloud system that shows interesting security properties. From here on, the graph can be used for manual or automatic, continuous, inspection.
Improving Cloud Security Certification
The way the CloudPG combines software- and infrastructure-layer has two central advantages in the context of cloud security certification: First, it improves the automation of security assessments, since results from different layers are already integrated. Second, in case of identified violations, it allows internal and external auditors to use the graph to get to the bottom of security flaws manually in a user-friendly way.
This way, we support the continuous assessment of cloud services and hope to simplify security audits in the cloud.
The CloudPG source code has been published as an open-source project on GitHub.
Furthermore, a scientific paper about the approach has been published in the proceedings of the 2021 IEEE 14th International Conference on Cloud Computing (CLOUD)

0 Comments